Introduction
The number of websites is increasing day by day on the internet, with an increase in web traffic the websites are more prone to cyber-attacks now. Web servers play a vital role to serve any website to end-user. As we know well Apache and Nginx are two majorly used web servers so let's discuss some of the security settings for these web servers.
There are a variety of security settings you can use to keep your websites and data secure on the web. In this article, we are going to cover some of the basic yet very effective security settings specific to Apache and Nginx web servers.
In the first part of this article, we will only discuss Apache specific security settings.
Pre-requisites
We have tested these settings on a CentOS-based system having Apache web server installed on it. Its hostname is apachehost and a website apachehost.com is hosted on it.
Note:
-
Let's assume that you have installed Apache using default package manager i.e yum or apt. If not then you might need to figure out the configuration files location.
-
These changes have been tested on the CentOS7-based system, steps may vary a little for Debian/Ubuntu-based systems.
-
Apache default config file location in RHEL/CentOS based systems is /etc/httpd/conf/httpd.conf.
-
Apache default config file location in Debian/ubuntu based systems is /etc/apache2/apache2.conf.
-
-
We are going to update Apache configurations so it is highly recommended to take a backup of the configuration files to make sure you can revert the changes in case something goes wrong.
-
We will mostly update Apache default configuration file httpd.conf. But these settings can be applied to website specific config files as well and with some other methods as well.
Below, we will discuss and apply some security settings for Apache step by step:
Hide Web Server Information
By default, Apache web server discloses some valuable information like a web server version which can help attacker leverage any known bug or vulnerability present in the specific version of the package.
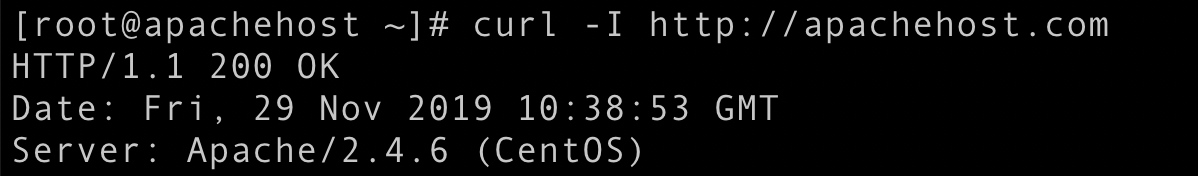
As shown in the image above anyone can easily identify the web server's version. We can prevent Apache to disclose this information:
Settings:
Make changes in Apache's default configuration /etc/httpd/conf/httpd.conf. Add the required code ServerSignature Off and ServerTokens Prod at the end of the file as shown below and save the file.

Now reload Apache service.
sudo service httpd reload
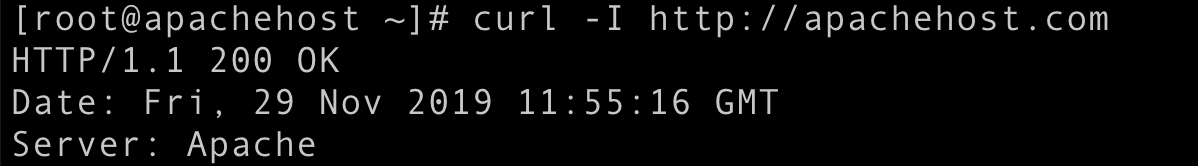
Test again using curl and you will see Apache is no longer disclosing the version.
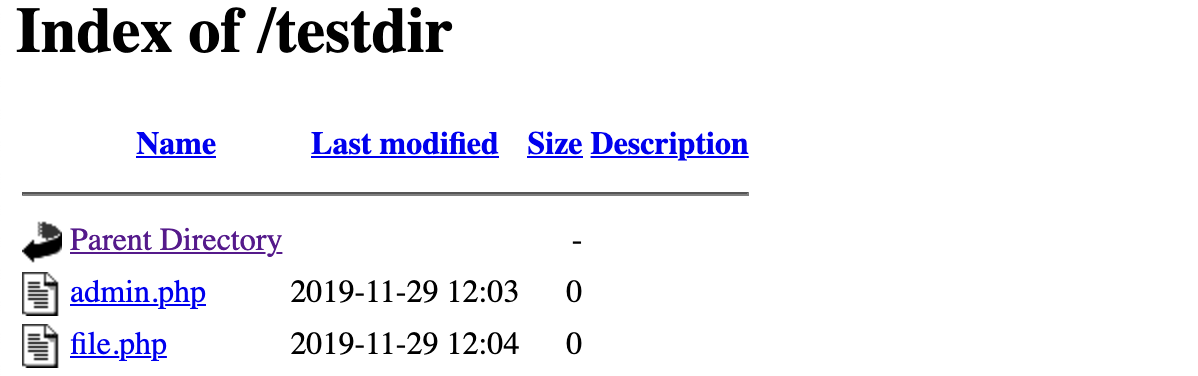
Disable Directory Listing
In the web server's document root if there is no index file then Apache will list all content presently there. As shown below in the image you will see all contents in the browser if directory listing is enabled, so the webserver can disclose some content unnecessarily.
Settings:
Make changes in Apache's default configuration /etc/httpd/conf/httpd.conf. Add the required code Options -Indexes as shown below and save the file. Note that you can also create a .htaccess file with this code under the same document root to disable directory listing.
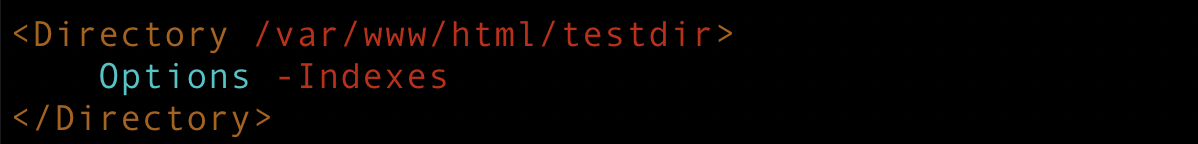
Now reload Apache service. Note that this setting may be overridden by the per-directory .htaccess files as specified in the documentation.
sudo service httpd reload
Test again in a browser, you should get a 403 Forbidden error.
Optimize SSL/TLS Settings
It is always recommended to run your website over https, however, it's not always enough to just set up an SSL certificate. There are some vulnerable SSL protocols and weak ciphers that we should disable to mitigate the risks.
Note: With these settings, your application might not support some legacy browsers. For more details please look into the detailed chart by Wikipedia about browsers compatibility with different SSL protocols.
Settings:
You can create a ssl.conf file under /etc/httpd/conf.d/ and add below-given code in it to disable weak SSL protocols and ciphers.
Now restart Apache service.
sudo service httpd restart
Qualys SSL Labs is a good tool to perform a deep analysis of SSL configuration. So you can test your live URL to identify how secure your SSL settings are.
Protection Against Cross-Site Scripting
Cross-site Scripting (XSS) is quite a common attack which is basically a client-side code injection. We can mitigate the risk of such attacks up to some level using X-XSS-Protection headers.
Note: These settings may impact your application functionality, please check here for more details about this header settings.
Settings:
Make changes in Apache default configuration /etc/httpd/conf/httpd.conf. Add the required code Header set X-XSS-Protection "1: mode=block" at the end of the file as shown below and save the file.

Now reload Apache service.
sudo service httpd reload
You can test using curl command if header is enabled:
curl --head http://apachehost.com
You should see X-XSS-Protection: 1; mode=block in the output.
Protection Against Clickjacking Attacks
Clickjacking is another type of attack to force users to download malware, access malicious links, visit malicious web pages, etc. Apache can use X-FRAME-OPTIONS in HTTP Header to prevent clickjacking attacks.
Note: There are different directives X-FRAME-OPTIONS header supports. We have only used SAMEORIGIN in our example below. Look for a detailed article about X-Frame-Options HTTP response header for more details about other directives and their possible impact on your website's functionality. Here is one of the good article by Mozilla.
Settings:
Make changes in Apache default configuration /etc/httpd/conf/httpd.conf. Add the required code Header always append X-Frame-Options SAMEORIGIN at the end of the file as shown below and save the file.
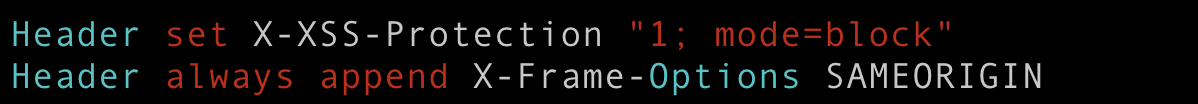
Now reload Apache service.
sudo service httpd reload
You can test using curl command if the header is enabled:
curl --head http://apachehost.com
You should see X-Frame-Options: SAMEORIGIN in the output.
Protection Against content-type sniffing
According to Wikipedia Content sniffing, also known as media type sniffing or MIME sniffing, is the practice of inspecting the content of a byte stream to attempt to deduce the file format of the data within it. Apache can use X-Content-Type-Options in HTTP Header to prevent content-type sniffing.
Note: These settings may impact your application functionality, please check here for more details about this header settings.
Settings:
Make changes in Apache default configuration /etc/httpd/conf/httpd.conf. Add the required code Header set X-Content-Type-Options nosniff at the end of the file as shown below and save the file.
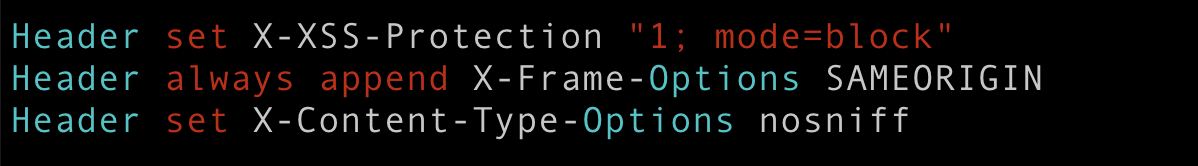
Now reload Apache service.
sudo service httpd reload
You can test using curl command if the header is enabled:
curl --head http://apachehost.com
You should see `X-Content-Type-Options: nosniff` in the output.
Enable IP based access
There can be a number of areas on your website that should be accessible to particular users only, like the admin area or maybe some backend dashboard. For example in a WordPress website /wp-admin is the area which should only be accessible to admin users. So to make it more secure we can enable IP based access to such areas/URLs. We will take an example of /wp-admin URL.
Settings:
Make changes in Apache default configuration /etc/httpd/conf/httpd.conf or your website specific conf file. Add the required code as shown below:
Now restart Apache service.
sudo service httpd restart
You should see a 403 Forbidden error if you try to access the wp-admin section from outside allowed IPs network.
As you can see these settings are quite simple to do but still, these are really helpful to keep secure your web server hence the websites it's serving. Also note that web server security is not limited to these settings only, what we have discussed in this article. Apart from these settings, there are a number of things you can take care of like setting up password protected directories, keeping your web server up to date, taking care of files/directories permissions, etc. In the next part of this blog series, we will discuss how we can implement these settings for Nginx web server.

Inderpreet Singh, Site Reliability Engineer - L2
Kindhearted cinema buff who loves reading, watching movies, and day dreaming about space exploration.



 We respect your privacy. Your information is safe.
We respect your privacy. Your information is safe.