Introduction
Before reading this blog post, we assume that you have already gone through part one of this blog series. In part one of this blog series, we discussed different security settings we can implement for web servers. And we followed the steps to implement those settings for the Apache web server. In this part of the blog series, we will follow the steps to implement those settings for the Nginx web server.
Pre-requisites
We have tested these settings on a CentOS-based system having an Nginx web server installed on it. For testing purposes only, we have set its hostname to nginxhost, and a website nginxhost.com is hosted on it.
Note
- Some of these settings may impact your application functionality; please go through part one of this blog series for more details.
- We assume that you have installed Nginx using default package manager i.e., yum or apt. If not, then you might need to figure out the configuration files location. These changes have been tested on CentOS7 based system, and steps may vary a little for Debian/Ubuntu-based systems.
- Nginx default config file location in RHEL/CentOS and Debian/Ubuntu-based systems is /etc/nginx/nginx.conf.
- We are going to update Nginx configurations, so it is highly recommended to take a backup of the configuration files to make sure you can revert the changes in case something goes wrong.
- We will mostly update the Nginx default configuration file nginx.conf. But these settings can be applied to website specific config files as well and with some other methods as well.
So below are the steps to apply some security settings for the Nginx web server:
Hide Web Server Information
Same as Apache, by default Nginx web server also discloses some valuable information like web server version, which can help attacker leverage any known bug or vulnerability present in the specific version of the package.
.png)
As shown in the image above, anyone can easily identify the web server version. We can prevent Nginx to disclose this information:
Settings
Make changes in Nginx’s default configuration /etc/nginx/nginx.conf. Add the required code server_tokens off under the HTTP configuration section, as shown below, and save the file.
.png)
Now reload the Nginx service.
sudo service nginx reload
Test again using curl command, and you will notice Nginx is no longer disclosing the version.
.png)
Disable Directory Listing
In Nginx, the by default directory listing is disabled, but still, it's good to check and confirm. As shown in the image below, you will see all contents in a browser if directory listing is enabled, so web servers can disclose some content unnecessarily.
.png)
Settings
Like we mentioned above, the by default directory listing is disabled in Nginx, you can check by browsing a location where there is no index file, you should get a 403 Forbidden error.
.png)
If Nginx is listing the contents of the directory, then make changes in Nginx default configuration /etc/nginx/nginx.conf. Under location directive, add the required settings autoindex off; as shown below:
.png)
Now reload Nginx service.
sudo service nginx reload
Test again in the browser. You should get a 403 Forbidden error.
Optimize SSL/TLS Settings
Note: With these settings, your application might not support some legacy browsers. For more details please look into the detailed chart by Wikipedia about browsers compatibility with different SSL protocols.
Settings
You can create a ssl.conf file under /etc/Nginx/conf.d/ directory and add below given code in it to disable weak SSL protocols and ciphers.
Now reload Nginx service.
sudo service nginx reload
Qualys SSL Labs is a good tool to perform a deep analysis of SSL configuration. You can test your live URL to identify how secure your SSL settings are.
Protection Against Cross-Site Scripting
Note: These settings may impact your application functionality, please check here for more details about this header settings.
Settings
Make changes in Nginx default configuration /etc/nginx/nginx.conf. Under the HTTP configuration section, add the required code add_header X-XSS-Protection "1; mode=block"; as shown below, and save the file.
.png)
Now reload Nginx service.
sudo service nginx reload
You can test using curl command if header is enabled:
curl --head http://nginxhost.com
You should see X-XSS-Protection: 1; mode=block in the output.
Protection Against Clickjacking Attacks
Note: There are different directives X-FRAME-OPTIONS header supports. We have only used SAMEORIGIN in our example below. Look for a detailed article about X-Frame-Options HTTP response header for more details about other directives and their possible impact on your website functionality. Here is one of the good article by Mozilla.
Settings
Make changes in Nginx default configuration /etc/nginx/nginx.conf. Under the HTTP configuration section, add the required code add_header X-Frame-Options "SAMEORIGIN"; as shown below and save the file.
.png)
Now reload Nginx service.
sudo service nginx reload
You can test using curl command if header is enabled:
curl --head http://nginxhost.com
You should see X-Frame-Options: SAMEORIGIN in the output.
Protection Against content-type sniffing
Note: These settings may impact your application functionality, please check here for more details about these header settings.
Settings
Make changes in Nginx default configuration /etc/nginx/nginx.conf. Under the HTTP configuration section, add the required code add_header X-Content-Type-Options nosniff; as shown below, and save the file.
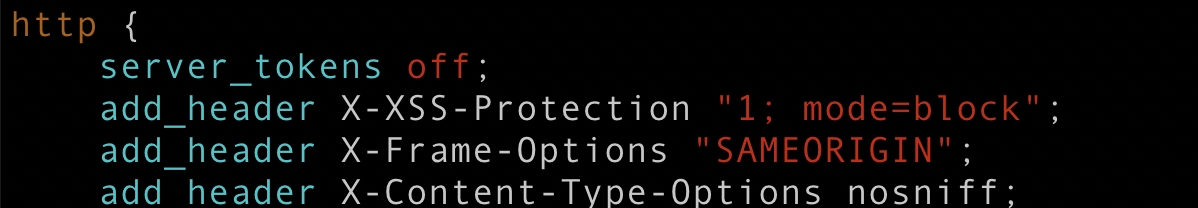
Now reload Nginx service.
sudo service nginx reload
You can test using curl command if header is enabled:
curl --head http://nginxhost.com
You should see `X-Content-Type-Options: nosniff` in the output.
Enable IP based access
Same as for Apache in part one of this blog series, we will use the example of /wp-admin URL.
Settings
Make changes in Nginx default configuration /etc/Nginx/nginx.conf or in your website specific conf file and add a location section as below:
Now reload Nginx service.
sudo service nginx reload
You should see 403 Forbidden errors if you try to access the wp-admin section from outside allowed IPs network.
Same as for Apache, these settings are quite simple to do for Nginx as well. Also, apart from these settings, there are a number of things you can take care of, like setting up password protected directories, keeping your web server up to date, taking care of files/directories permissions, etc. for Nginx as well. This was the last part of this blog series. I hope this will help you to run your web applications securely on these web servers.
If you have directly jumped into this part of this blog series, I highly recommend you go through part one as well.

Inderpreet Singh, Site Reliability Engineer - L2
Kindhearted cinema buff who loves reading, watching movies, and day dreaming about space exploration.

 We respect your privacy. Your information is safe.
We respect your privacy. Your information is safe.



Leave us a comment